Citing the Reddit remark, Beaumont took to Mastodon to clarify: “Persons are fairly brazenly posting what is occurring on Reddit now, menace actors are registering rogue FortiGates into FortiManager with hostnames like ‘localhost’ and utilizing them to get RCE.”
Beaumont wasn’t instantly obtainable to elaborate. In the identical thread, one other consumer mentioned that primarily based on the transient description, it seems attackers are one way or the other stealing digital certificates authenticating a tool to a buyer community, loading it onto a FortiGate machine they personal, after which registering the machine into the client community.
The particular person continued:
From there, they will configure their means into your community or presumably take different admin actions (eg. presumably sync configs from reliable managed units to their very own?) It is not tremendous clear from these threads. The mitigation to forestall unknown serial numbers suggests {that a} speedbump to quick onboarding prevents even a cert-bearing(?) machine from being included into the fortimanager.
Beaumont went on to say that primarily based on proof he’s seen, China-state hackers have “been hopping into inside networks utilizing this one since earlier within the yr, appears like.”
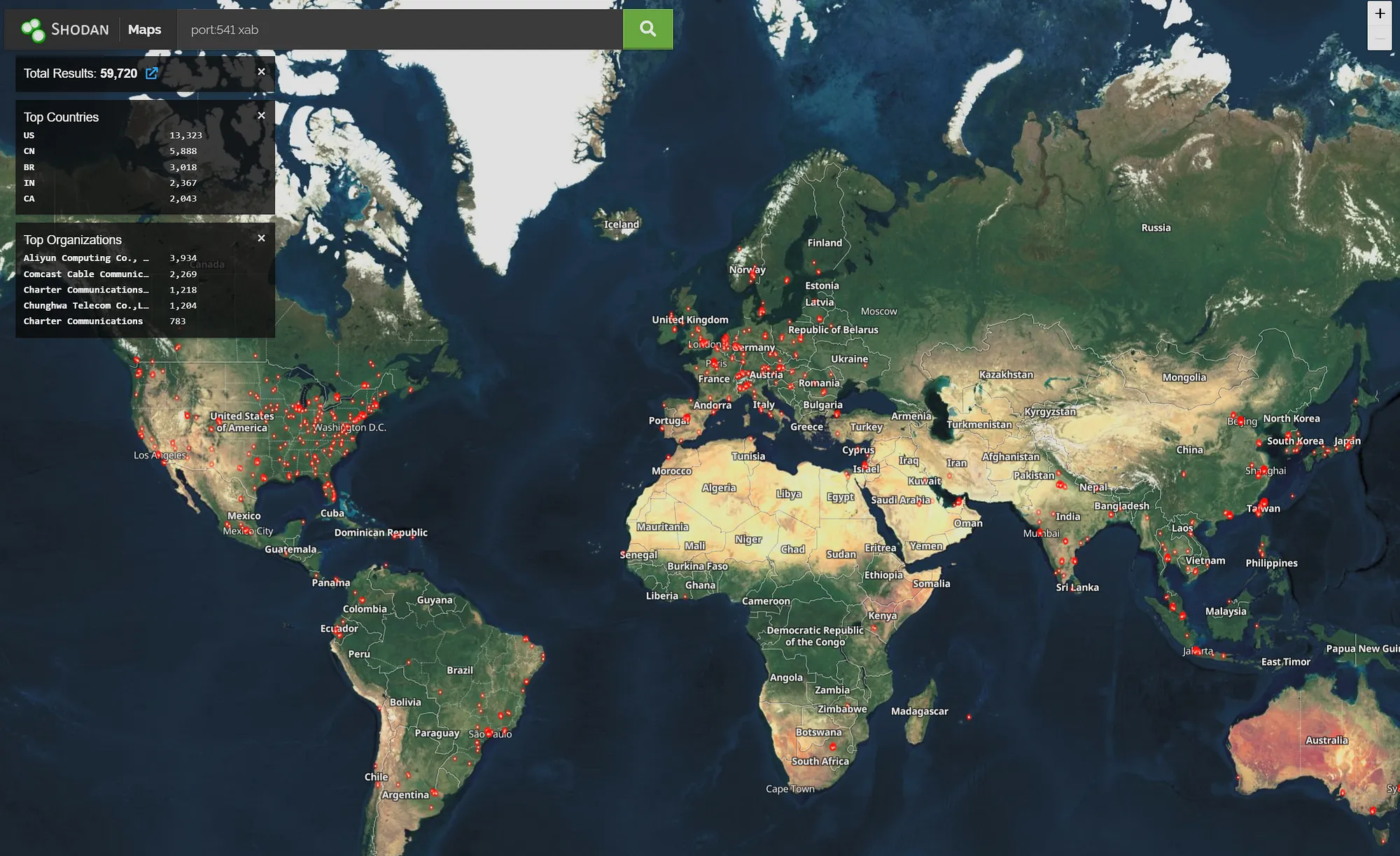
60,000 units uncovered
After this publish went dwell on Ars, Beaumont revealed a publish that mentioned the vulnerability doubtless resides within the FortiGate to FortiManager protocol. FGFM is the language that enables Fortigate firewall units to speak with the supervisor over port 541. As Beaumont identified, the Shodan search engine reveals greater than 60,000 such connections uncovered to the Web.
Beaumont wrote:
There’s one requirement for an attacker: you want a legitimate certificates to attach. Nonetheless, you’ll be able to simply take a certificates from a FortiGate field and reuse it. So, successfully, there’s no barrier to registering.
As soon as registered, there’s a vulnerability which permits distant code execution on the FortiManager itself through the rogue FortiGate connection.
From the FortiManager, you’ll be able to then handle the legit downstream FortiGate firewalls, view config recordsdata, take credentials and alter configurations. As a result of MSPs — Managed Service Suppliers — typically use FortiManager, you should use this to enter inside networks downstream.
Due to the way in which FGFM is designed — NAT traversal conditions — it additionally means if you happen to acquire entry to a managed FortiGate firewall you then can traverse as much as the managing FortiManager machine… after which again right down to different firewalls and networks.
To make issues tougher for FortiGate clients and defenders, the corporate’s assist portal was returning connection errors on the time this publish went dwell on Ars that prevented folks from accessing the location.