Google researchers stated they uncovered a Kremlin-backed operation focusing on recruits for the Ukrainian army with information-stealing malware for Home windows and Android gadgets.
The malware, unfold primarily by means of posts on Telegram, got here from a persona on that platform often known as “Civil Protection.” Posts on the @civildefense_com_ua telegram channel and the accompanying civildefense[.]com.ua web site claimed to offer potential conscripts with free software program for locating user-sourced areas of Ukrainian army recruiters. In reality, the software program, accessible for each Home windows and Android, put in infostealers. Google tracks the Kremlin-aligned menace group as UNC5812.
Twin espionage and affect marketing campaign
“The final word intention of the marketing campaign is to have victims navigate to the UNC5812-controlled ‘Civil Protection’ web site, which advertises a number of totally different software program applications for various working methods,” Google researchers wrote. “When put in, these applications outcome within the obtain of varied commodity malware households.”
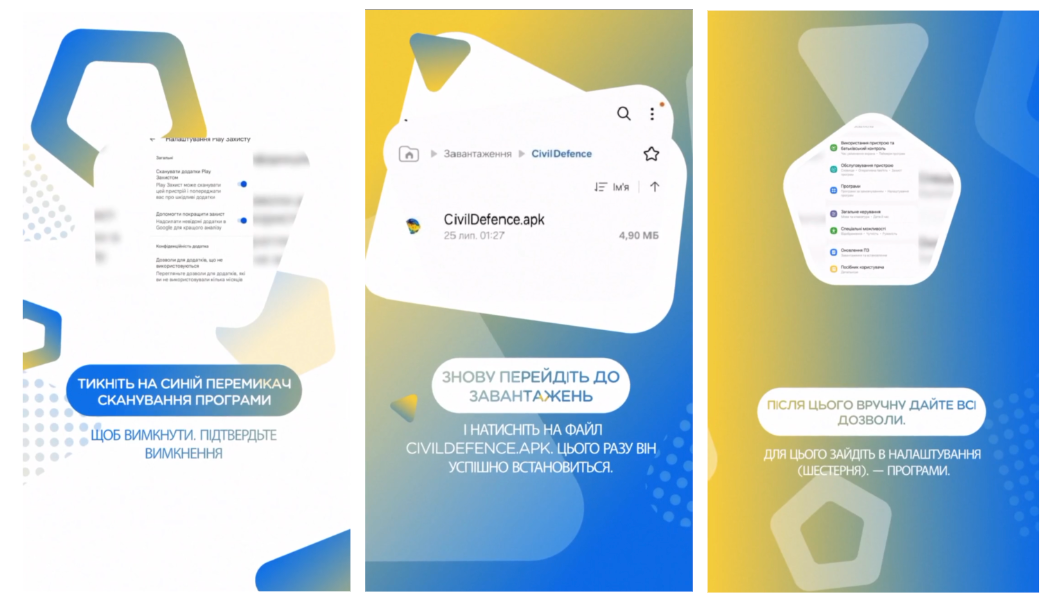
The Android variations used social engineering to trick customers into turning off Play Defend, a Google service that routinely scans gadgets for malware, whether or not from Play or third-party sources. Throughout set up, the app additionally offered reassurances that the scary system privileges being requested had been mandatory to guard the protection of customers.
Photos justifying why permissions and bypassing of Play Defend are mandatory.
Credit score:
An FAQ on the web site additionally contained a “strained” justification for the Android app not being accessible in Play, however somewhat solely as a side-load downloaded from the location. The justification is designed to preempt frequent safety recommendation that Android customers keep away from sideloaded apps and procure apps solely from Play.
The campaigns for Home windows and Android relied on off-the-shelf infostealers. The Android infostealer is a variant of CraxsRat, a package deal that implements many backdoor functionalities sometimes present in Android backdoors.
The Home windows malware, in the meantime, used a customized model of Pronsis Loader, which was found final month by safety agency Trustwave, to put in PureStealer, accessible on the market on-line for $150 a month or $699 for a lifetime license.
The Civil Protection web site additionally advertises help for macOS and iOS, however variations for these platforms weren’t accessible on the time of study.
The Google researchers wrote: